Blockchains - Overview, Features, Structure, Part 1 of 2
By: Peter Chipkin

Article Contents
- A Few Definitions
- 4 Elements make the Blockchain
- Byzantine Fault Tolerance
- Decentralized Nodes and Replicated Ledgers
- Nodes
- The Blocks of the Block Chain
- The Consensus Rules
- Three Kinds of Consensus for Blockchain
- Types of Consensus Algorithms
The characteristic known as " Byzantine fault tolerance " (BFT) is one of those concepts worth understanding. The ability to tolerate what computer scientists call "byzantine failures" is a crucial part of blockchains' ability to maintain reliable records of transactions in a transparent, tamper-proof way.
Imagines a group of Byzantine generals and their armies surrounding a castle and preparing to attack. To be successful, these armies must all attack at the same time. But they know that there is a traitor in their midst. A traitor who can make different commitments to different his fellow generals about when he will or wont attack.
The important thing is that every general agrees on a common decision, for a halfhearted attack by a few generals would become a defeat and be worse than a coordinated attack or a coordinated retreat. But how can they rely when they know there is a traitor.
The problem is complicated further by the generals being physically separated and having to send their votes via messengers who may fail to deliver votes or may forge false votes.
You may be wondering what any of this has to do with computers.
In any distributed computing environment, meaning an environment where multiple users, applications, servers or other types of nodes compose the environment (like a blockchain), there is a risk that rogue or unreliable actors could cause the environment to break apart.
In order to be reliable, a distributed computing environment has to be designed in a way that solves the Byzantine generals' problem by providing what's known as BFT.
The answer – There are many solutions.
Many influential blockchain systems, including Bitcoin, have relied on a concept called proof of work (PoW). Under this model, anyone who wants to add to the blockchain must perform a work-intensive task using information from the existing blockchain in order to add new information. In the case of Bitcoin, PoW is produced using a hashing algorithm that, by its nature, takes a fair amount of time to execute.
It's more important to understand the problem that is solved than to understand the details of the solution. So don't fixate on this topic.
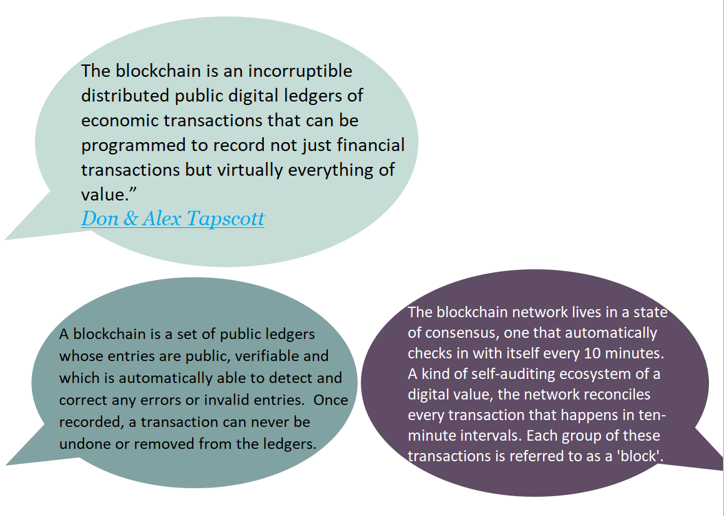
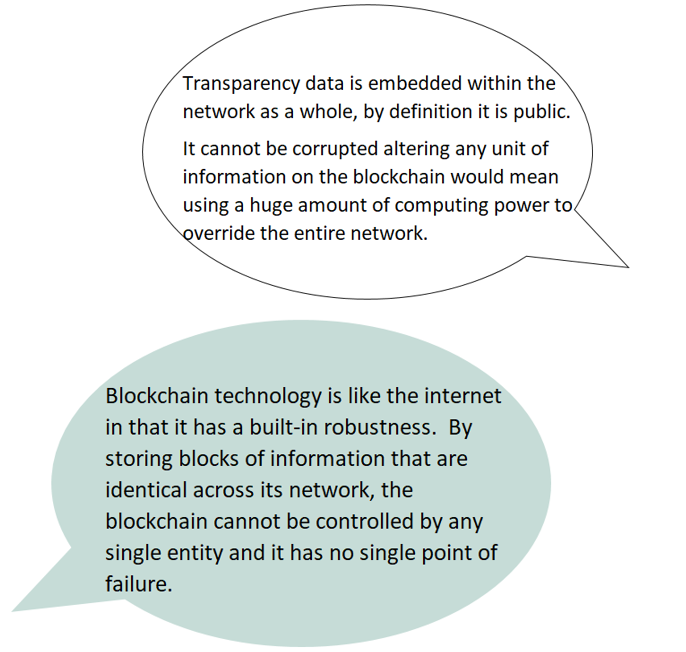
By storing data across its network, the blockchain eliminates the risks that come with data being held centrally.
Its network lacks centralized points of vulnerability that computer hackers can exploit. Today's internet has security problems that are familiar to everyone. We all rely on the "username/password" system to protect our identity and assets online. Blockchain security methods use encryption technology.
The basis for this are the so-called public and private "keys". A "public key" (a long, randomly-generated string of numbers) is a users' address on the blockchain. Bitcoins sent across the network gets recorded as belonging to that address. The "private key" is like a password that gives its owner access to their Bitcoin or other digital assets. Store your data on the blockchain and it is incorruptible. This is true, although protecting your digital assets will also require safeguarding of your private key by printing it out, creating what's referred to as a paper wallet.
Computer connected to the blockchain network using a client that performs the task of validating and relaying transactions gets a copy of the blockchain, which gets downloaded automatically upon joining the blockchain network.
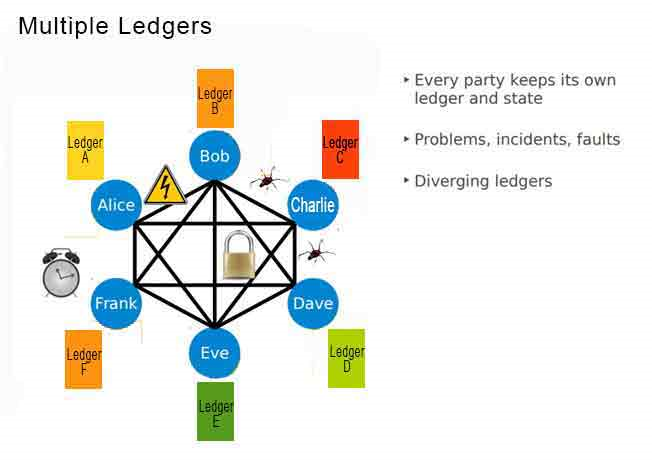
Every node is an "administrator" of the blockchain, and joins the network voluntarily (in this sense, the network is decentralized).
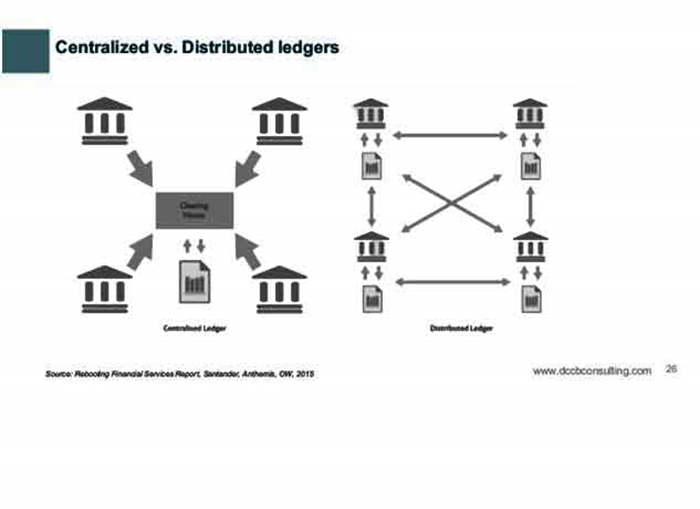
A global network of computers uses blockchain technology to jointly manage the database that records Bitcoin transactions. That is, Bitcoin is managed by its network, and not any one central authority. Decentralization means the network operates on a user-to-user (or peer-to-peer) basis. The forms of mass collaboration this makes possible are just beginning to be investigated.
The nodes in the overall network use the peer-to-peer IP network to process and verify transactions. When several nodes all have the same blocks in their individual databases, they are considered to be in consensus.
Every node maintains a fully replicated copy of a database that contains the payment history of every bitcoin ever created along with ownership information. As transactions happen using the currency, a consensus mechanism essentially dictates how nodes agree on blockchain updates.
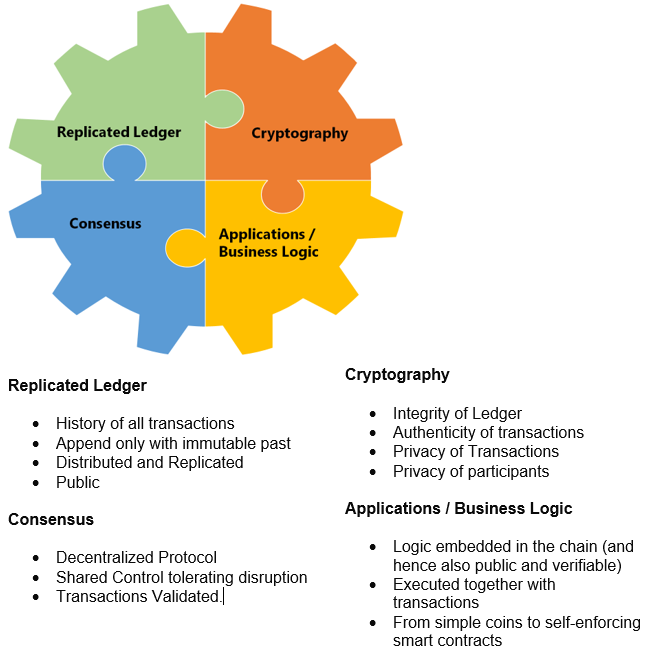
The term Blockchain is derived from a design pattern that describes a chain of data blocks that map to individual transactions. Each transaction that is conducted in the real world (e.g a Bitcoin wire transfer) results in the creation of new blocks in the chain. The new blocks so created are done so by calculating a cryptographic hash function of its previous block thus constructing a chain of blocks – hence the name.
The blockchain is a linked list of blocks which contains data and a hash pointer which points to its previous block, hence creating the chain.

Blockchain Platform:
The Blockchain itself is an application that runs on a network of distributed servers.
The core application is a transaction database modeled as a secure ledger, that is shared by all nodes (servers) that run the full stack install. It is thus a 100% decentralized transaction system that acts as a highly transparent ledger. Any node running the Blockchain software can run the entire Blockchain locally.
Once installed on a server, the full Blockchain client syncs up with other nodes in the network. From then onwards the particular server maintains all and any transaction records conducted using bitcoins (or any other application running on the Blockchain). The integrity and chronological order of the transactions (& the addresses owning the currency) are enforced by strong cryptographic rules.
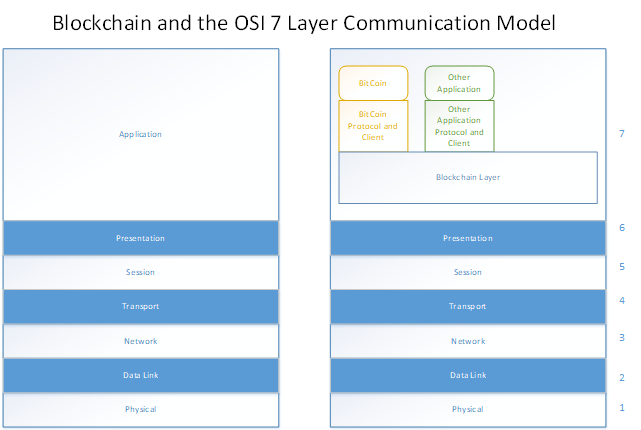
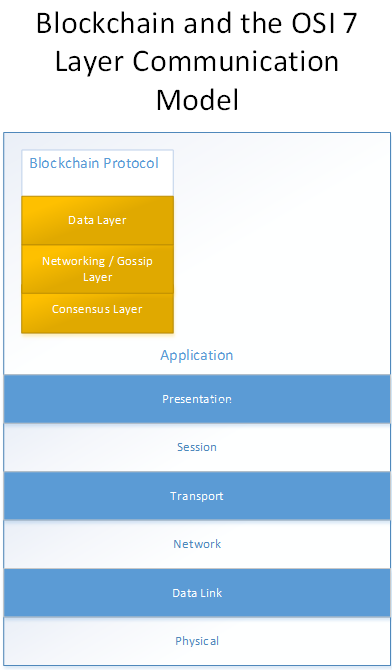
Network Protocol Stack : Once nodes are booted up, they perform a peer discovery to contact any other valid node using a given port over TCP. The Blockchain stack is depicted below and is layered on the OSI stack. The Blockchain Message Exchange specifies the handshake logic between nodes as well as the serialization format for messages exchanged over the wire.
The Blockchain Overlay Network provides higher level semantics that allow multiple types of blockchains (public, vertical specific & private blockchains) to co-exist as well as provides management abstraction for the same. Developers will essentially use this layer to extend vanilla blockchain to support other kinds of applications which can leverage the existing bitcoin blockchain to validate their transactions. E.g. Other kinds of virtual currency, sidechains etc.
The consensus rules are block chains most important rules. They establish – among many other things
· The amount of reward (like Bitcoins) that mining a block will produce
- The mining difficulty
- The type of proof of work required
- Block size limits (like the 21milllion Bitcoins)
- How many nodes to check that a block is valid
These rules are agreed by a convention of core programmers and implemented in the platform. When they do not agree then the chain forks. One with one set of rules and other with different rules.

1. Decentralized / permission less – Bitcoin, Ethereum
· Survives censorship and suppression - No central entity
· Nakamoto consensus requires proof-of-work (PoW) - Original intent: one CPU, one vote - Majority of hashing power controls network - Gives economic incentive to participate (solution to PoW is a newly "mined" Bitcoin)
· Today, total hashing work consumes a lot of electricity - Estimates vary, 250-1000MW, from a major city to a small country ...
· Protocol features - Stability is a tradeoff between dissemination of new block (10s-20s) and mining rate (new block on average every 10min) - Decisions are not final ("wait until chain is 6 blocks longer before a tx is confirmed")
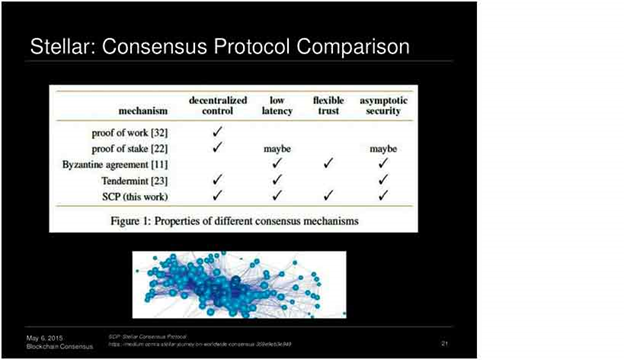
2. Somewhat decentralized – Ripple, Stellar
- Nodes decide whom to trust – Validator nodes
· Quorum-like protocol – Among different heterogeneous validators
· Consistent when "enough" nodes in path are trusted by the nodes involved in the transaction
· Transactions among two nodes are agreed if validated by "strong" majority in the overlap of the trusted node sets – In practice, leads to centralization
3. Consortium / permissioned – BFT (Byzantine fault tolerance) consensus
1. Proof of work
2. Proof of stake
3. Proof of activity
4. Proof of burn
5. Proof of capacity
Key cryptography problems in distributed networks remain unsolved or solutions are untested on a robust scale.
One size consensus does not fit all applications. Proof of Work mining is not the best consensus protocol for enterprise (IOT) applications. These applications require faster, cheaper settlement, legal identity verification, scalability and performance.
GO TO THE NEXT ARTICLE (Part 2)