Control Systems Vulnerabilities

While new control technology can be very handy, it is also flawed. Here are some
articles to help you understand these flaws and inform you on how to better protect yourself from being
targeted.
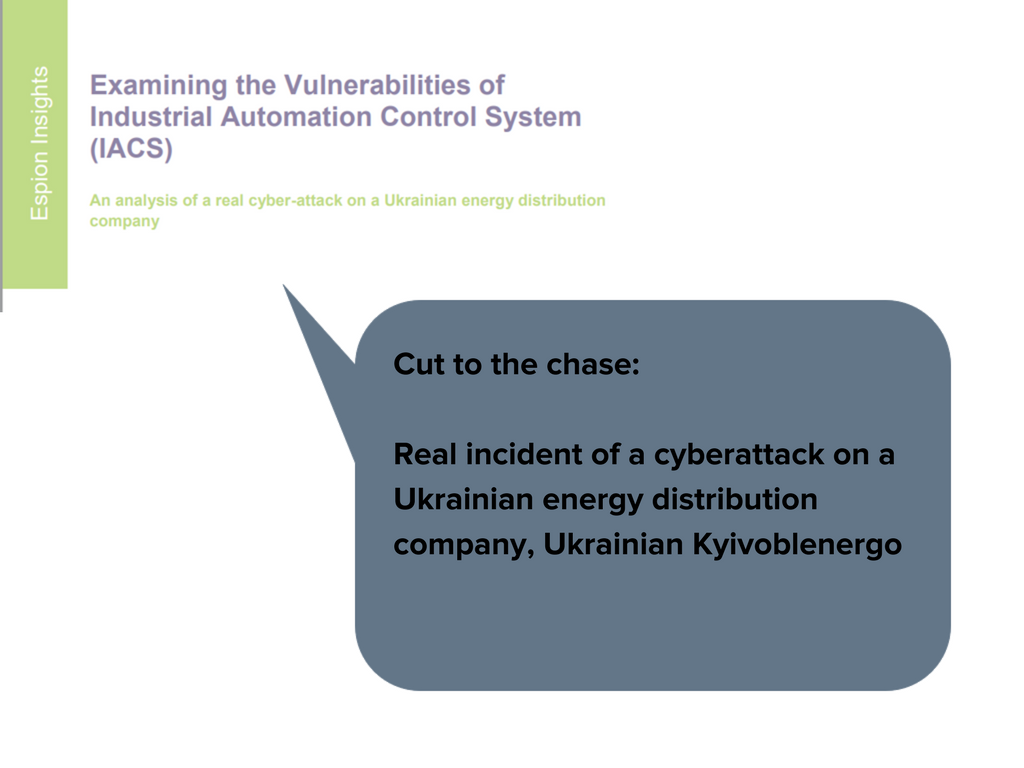
Read the full article here: Examining_the_Vulnerabilities_of_Industrial_Automation_Control_System_(IACS).pdf
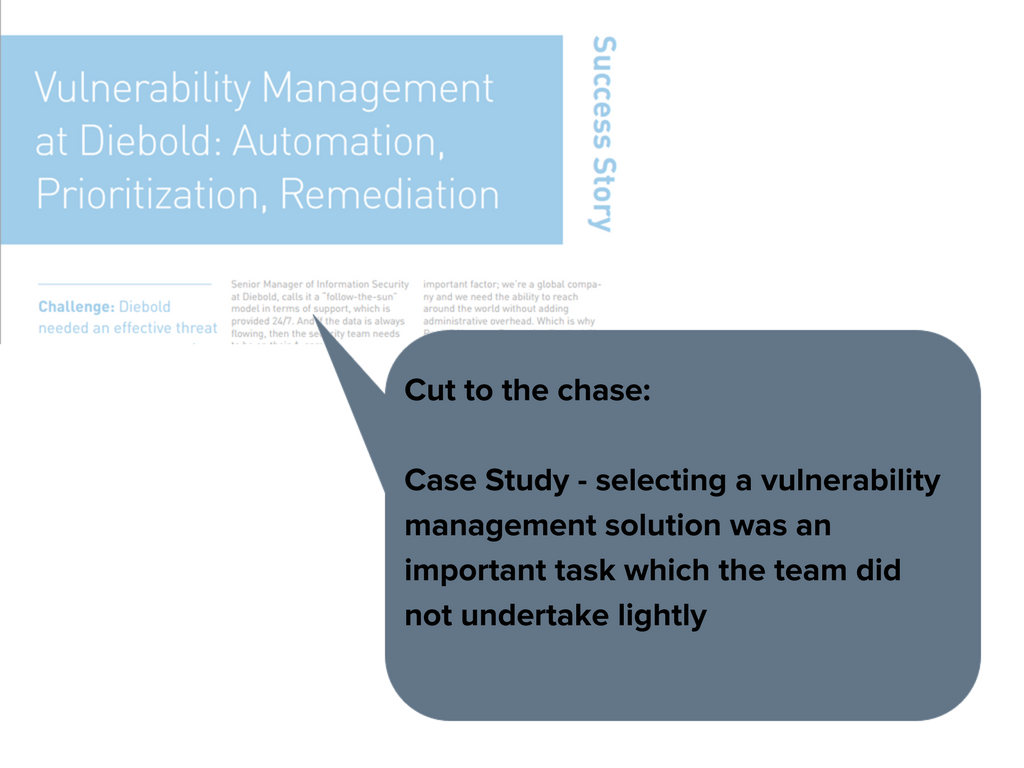
Read the full article here: https://www.rapid7.com/docs/cs-diebold.pdf
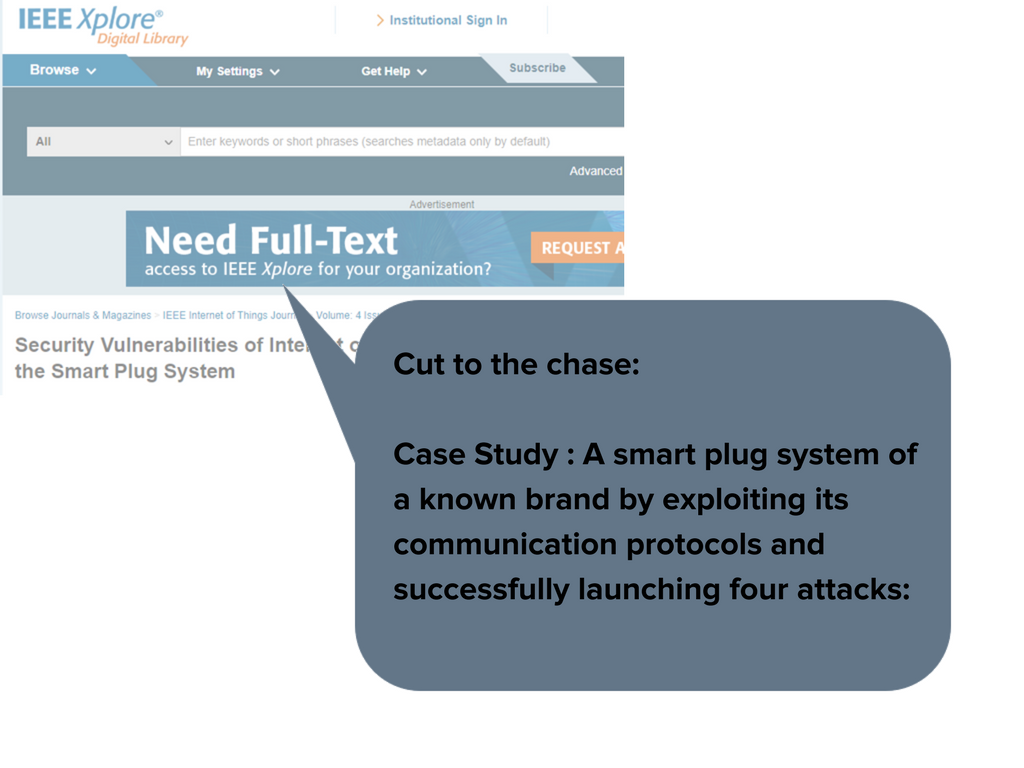
Read the full article here: http://ieeexplore.ieee.org/document/7932855/
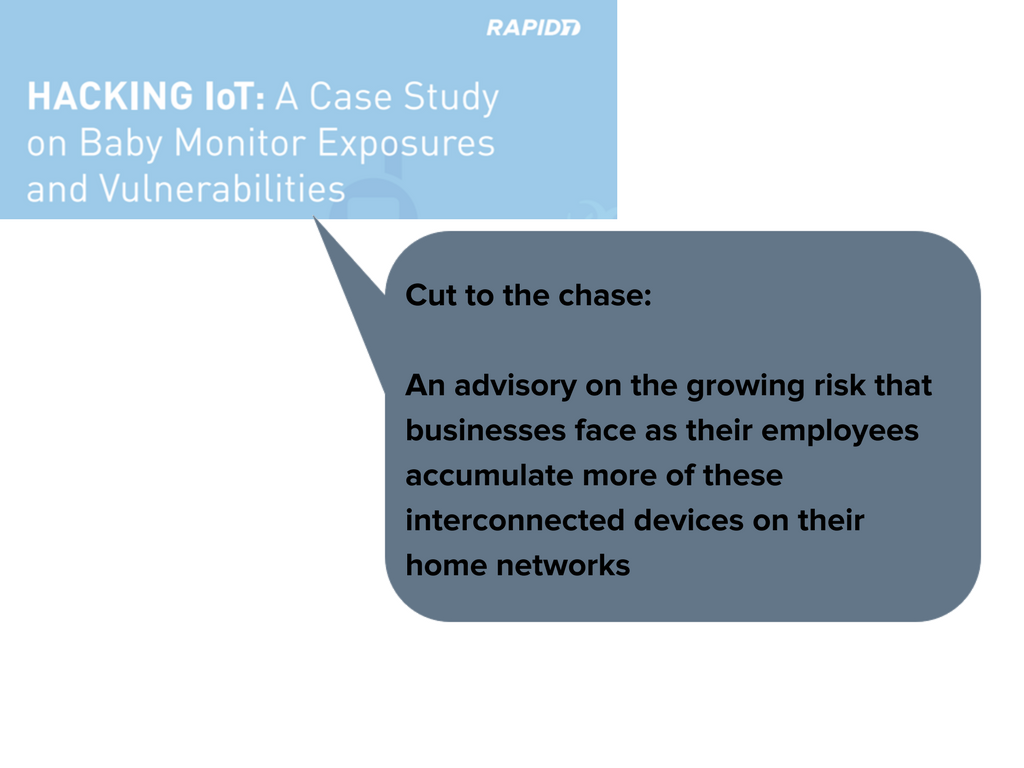
Read the full article here: https://www.rapid7.com/docs/Hacking-IoT-A-Case-Study-on-Baby-Monitor-Exposures-and-Vulnerabilities.pdf
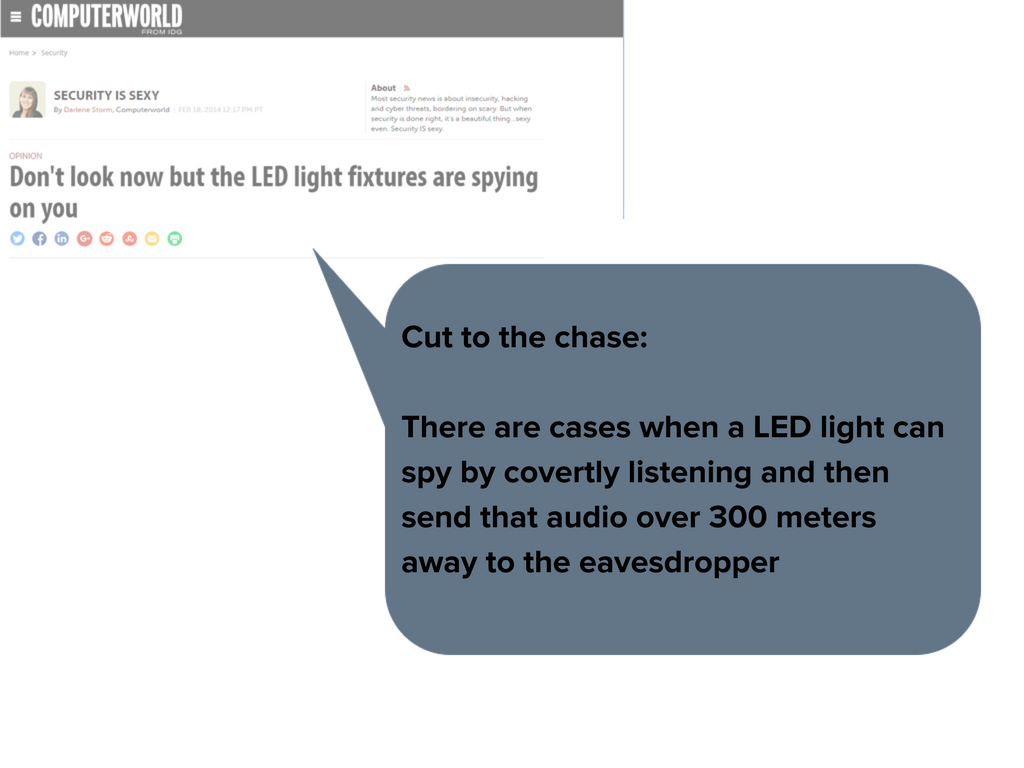
Read the full article here: https://www.computerworld.com/article/2475911/security0/don-t-look-now-but-the-led-light-fixtures-are-spying-on-you.html

Read the full article here: https://www.iotforall.com/5-worst-iot-hacking-vulnerabilities/
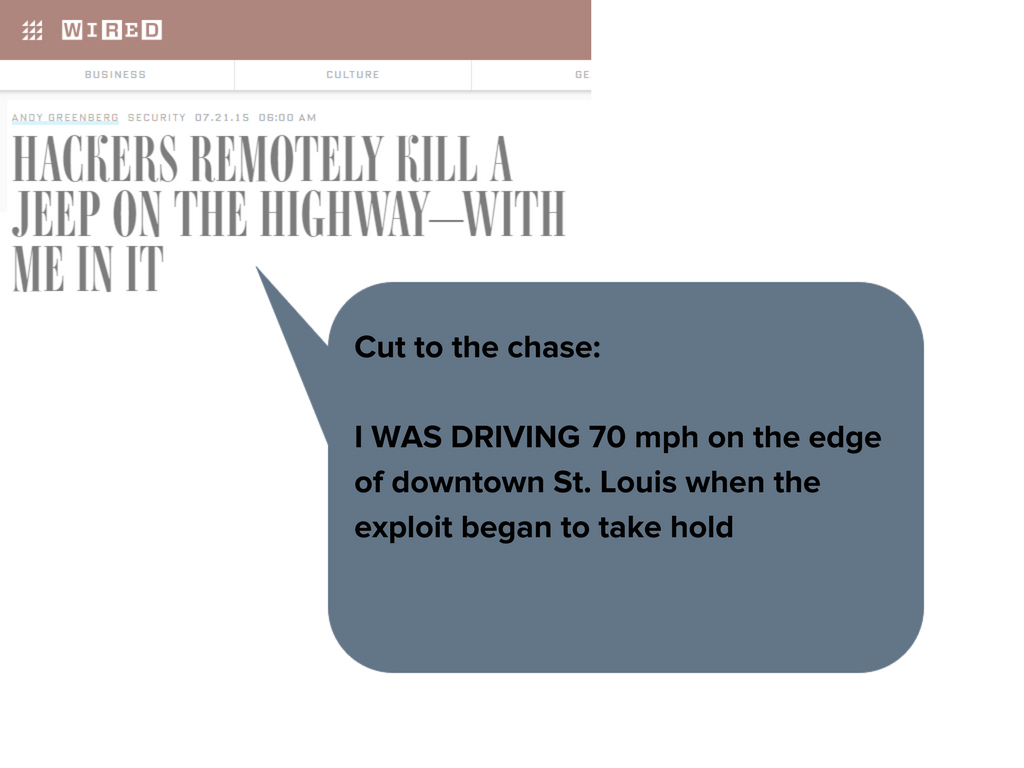
Read the full article here: https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/
<---- Previous Article Main Page