EnOcean Security Model
EnOcean Security Model
The EnOcean standard 868 MHz sensor modules integrate these state-of-the-art data encryption mechanisms to meet the requirements of specific applications such as monitoring or alert sensor systems. These enhanced security mechanisms can optionally be activated to prevent different types of attacks, including replay and eavesdropping attacks or forging of messages. Shipped in standard mode, the encrypted data transmission can be activated by simply pressing the learn button for ten seconds. If needed, the security mode can be deactivated by pressing and holding the learn button again. Also a receiver that decodes encrypted telegrams can still process standard telegrams enabling OEMs to effortlessly include enhanced data security in their existing EnOcean-based portfolio.
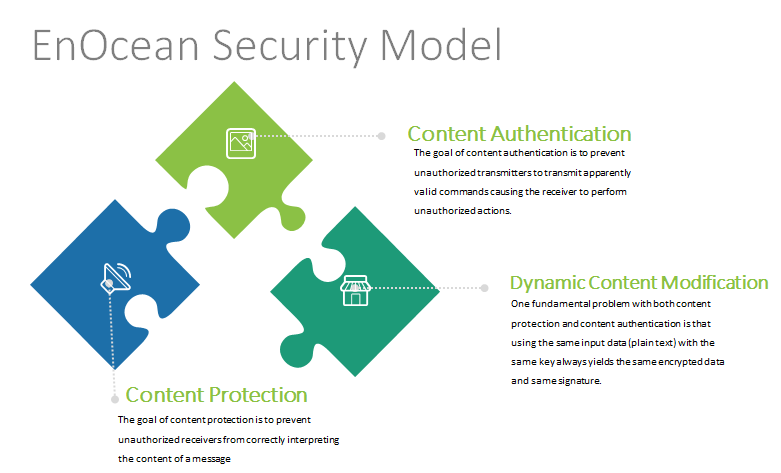
One fundamental problem with both content protection and content authentication is that using the same input data (plain text) with the same key always yields the same encrypted data and same signature. In order to prevent this type of attack, either the data or the key must continuously change to ensure that identical input data does not create The mechanism used by the transmitter to change data or key must be known to the receiver in order to correctly decrypt and authenticate received data telegrams. One common approach is to use the secret key together wit to generate a dynamic key.
Summary
1. Feature: content protection – implemented with: data encryption
2. Feature: content authentication – implemented with: CMAC – cipher based
message authentication
3. Feature: dynamic content modification – implemented with: RLC – rolling
code