Finding what Applications use what Port
When troubleshooting network communication issues on Windows systems, it is often necessary to determine which application or service is bound to a specific TCP or UDP port. This is particularly important when diagnosing port conflicts, verifying that a service is listening as expected, or confirming which process is responsible for open network connections.
Windows provides built-in command-line tools that expose this information without requiring third-party
software. The most commonly used tool for this purpose is netstat, which can display active
connections, listening ports, and the process identifiers (PIDs) associated with each connection.
The steps below describe a straightforward method to identify which applications are using which ports on
a Windows system by correlating netstat output with the Windows Task Manager.
Using Netstat to List Active Ports
The netstat command is available on all modern versions of Windows and provides detailed
information about network activity. To begin, open the Windows Command Prompt with appropriate privileges.
Administrative rights may be required to see all processes.
At the command prompt, enter the following command:
netstat -ano
This command displays a list of all active TCP connections and listening ports, along with the numerical address information and the process ID associated with each entry.
- -a: Displays all active TCP connections and all TCP and UDP ports on which the computer is listening.
- -n: Displays addresses and port numbers in numerical form, without attempting name resolution.
- -o: Displays the owning process ID (PID) for each connection.
These parameters are commonly combined because they provide a complete, unambiguous view of network activity suitable for diagnostic work.
Mapping Ports to Applications Using Task Manager
Once the netstat -ano command has been executed, identify the port of interest in the output.
Note the corresponding PID listed in the final column. The PID uniquely identifies the process that owns
the connection or listening socket.
Next, open the Windows Task Manager. Navigate to the Processes tab (or Details tab on newer versions of Windows) and locate the process with the matching PID. This allows you to determine the executable name and, in many cases, the associated application or service.
If the PID column is not visible in Task Manager, enable it by selecting the View menu,
choosing Select Columns, and ensuring that PID (Process Identifier) is
checked. Once enabled, the PID values can be directly compared to the netstat output.
Example Output
The image below shows a sample netstat output where active connections and listening ports are
displayed along with their associated PIDs. This visual correlation is useful when validating that a
specific service is bound to the expected port or when identifying unexpected listeners.
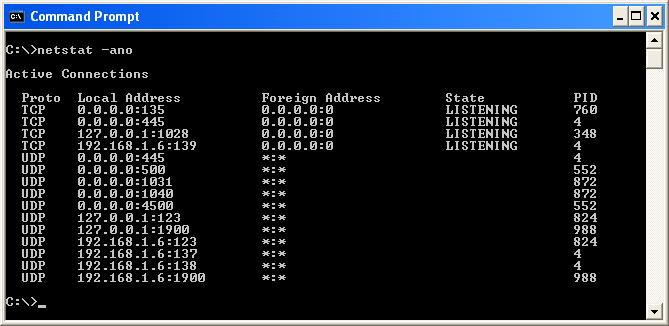
In environments involving automation software, protocol gateways, or test tools, this method is frequently used to confirm that communication services are running correctly and not blocked or duplicated by other processes.
FAQ
Does this method work for both TCP and UDP ports?
Yes. The -a option causes netstat to display both TCP and UDP listening ports and
active connections.
Why do some ports show a PID but no obvious application name?
Some ports may be owned by system services or background processes. In these cases, Task Manager may show
a generic service host or system process rather than a user-facing application.
Is this approach limited to Windows?
This specific workflow applies to Windows. Unix-like operating systems provide similar functionality using
tools such as netstat, ss, or lsof, but the commands and outputs differ.
Why is identifying port usage important in control and automation systems?
Control systems often rely on fixed or well-known ports. Identifying which application is bound to a port
helps diagnose communication failures, misconfigurations, and unintended service exposure.
Integration Solutions
Chipkin has integration solutions for almost every situation. We specialize in network protocol communications and have over 20+ years of experience. Click for more information:
