Honeypots a Complete Guide

Contents:
1. Overview
2. Different types of Honeypots?
3. What are Honeynets, how is it different than honeypots?
4. Could honeypots be setup wirelessly?
5. How to configure/Setup a simple Honeypot?
6. Advantages and Disadvantages of setting up a honeypot.
7. Ethical concerns related to honeypots!!
8. Firewall and Honeypots. How they inter-work together?
9. Honeypots securing SCADA network, how?
10. Honeypot & automation, a bigger game!! - Communication protocols - PLC, FTP, Modbus etc., – let's see!

1. Overview:
With the day to day growth of internet users in an information revolution, how secure are we and our data?
From social media to banking, everything is over internet!
How to protect our valuable data from hackers? What are HONEYPOTS? What has that got to do with the security of the data? Let's check it out.
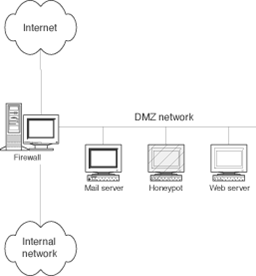
Fig: Network diagram of a honeypot deployed on a DMZ to detect attacks
Well what are honeypots?
It is a decoy computer system that simulates the behavior of a real system having data that seems to be legitimate part of the network/site, but it is actually isolated and closely monitored for trapping hackers or tracking unconventional or new hacking methods, who are then blocked/trapped.
The main purpose of a Honeypot is to detect and learn from the attacks and further use the information to improve security.
Why Honeypots??
The value/worth of the honeypots depends on the information that could be gathered from it. There are two popular reasons for setting up a Honeypot:
- Gain Understanding
To understand how hackers probe and attempt to gain access to your systems. Since a record of the hacker activities are kept, one can gain understanding of the attack methodologies incorporated and improve the security of the network/system by eliminating the loopholes.
- Gather Information
Gather forensic information that is needed to aid in the prosecution of hackers. This is the sort of information which is often needed to provide law enforcement officials with the details needed to prosecute.
Honeypots can also protect an organization from insider threats. According to the 2016 Cyber Security Intelligence Survey, IBM found that 60% of all attacks were carried by insiders.
2. Types of honeypots:
There are mainly two types of honeypots based on the use-case scenario:
1. Research Honeypots
2. Production Honeypots
Research Honeypots:
- These are mainly used or deployed to gather information and understand about the various attack methodologies, tactics used by the intruders to gain access into a system/network.
- These honeypots doesn't add direct value to any specific organization, but the information helps in improving their security.
- Research honeypots are complex in maintenance and deployment and primarily used by military, research and government organizations.
- For example, the Honeynet Project is a volunteer, nonprofit security research organization that uses honeypots to collect information on cyber threats.
Production Honeypots:
- These are primarily used for detection and to protect organizations. The main purpose of a production honeypot is to help mitigate risk in an organization
- Increasingly, however, production honeypots are being recognized for the detection capabilities they can provide and for the ways they can supplement both network- and host-based intrusion protection.
- They are typically easy to deploy and gathers only limited information and primarily used by corporations.
- Production honeypots are placed inside the production network with other production servers by an organization to improve their overall state of security.
Further Based on design criteria of the honey pots are further classified as:
1. Pure honeypots
2. High-interaction honeypots
3. Low-interaction honeypots
Pure honeypots are full-fledged production systems. The activities of the attacker are monitored by using a bug tap that has been installed on the honeypot's link to the network. No other software needs to be installed. Even though a pure honeypot is useful, stealthiness of the defense mechanisms can be ensured by a more controlled mechanism.
High-interaction honeypots imitate the activities of the production systems that host a variety of services and, therefore, an attacker may be allowed a lot of services to waste his time. By employing virtual machines , multiple honeypots can be hosted on a single physical machine. Therefore, even if the honeypot is compromised, it can be restored more quickly. In general, high-interaction honeypots provide more security by being difficult to detect, but they are expensive to maintain. If virtual machines are not available, one physical computer must be maintained for each honeypot, which can be exorbitantly expensive. Example: Honeynet .
Low-interaction honeypots simulate only the services frequently requested by attackers. Since they consume relatively few resources, multiple virtual machines can easily be hosted on one physical system, the virtual systems have a short response time, and less code is required, reducing the complexity of the virtual system's security. Example: Honeyd.
Source: www.wikipedia.com
3. What are Honeynets? How is it different than honeypots?
Two or more honeypots on a network form a honeynet. In some cases only one honeypot will not be sufficient (example: databases, ATCs) therefore a honeynet plays a vital role monitoring the entire network at a larger scale.
Honey nets and honeypots are usually implemented as parts of larger network intrusion detection systems.
In addition to the honey pots, a honeynet usually has real applications and services so that it seems like a normal network and a worthwhile target. However, because the honeynet doesn't actually serve any authorized users, any attempt to contact the network from without is likely an illicit attempt to breach its security, and any outbound activity is likely evidence that a system has been compromised.
For this reason, the suspect information is much more apparent than it would be in an actual network, where it would have to be found amidst all the legitimate network data. Applications within a honeynet are often given names such as "Finances" or "Human Services" to make them sound appealing to the attacker.
A honey farm is a centralized collection of honeypots and analysis tools. A virtual honeynet is one that, while appearing to be an entire network, resides on a single server.
4. Could honeypots be setup wirelessly?
Yes, you can- With the exponentially increasing usage of wireless devices, the threat of wireless attacks is also growing. The goal of deploying wireless honeypots is to capture behaviors of our system in a wireless area and obtain some information and statistics.
Honeyspot is the well-known wireless honeypot project supported by Spanish Honeynet Project.
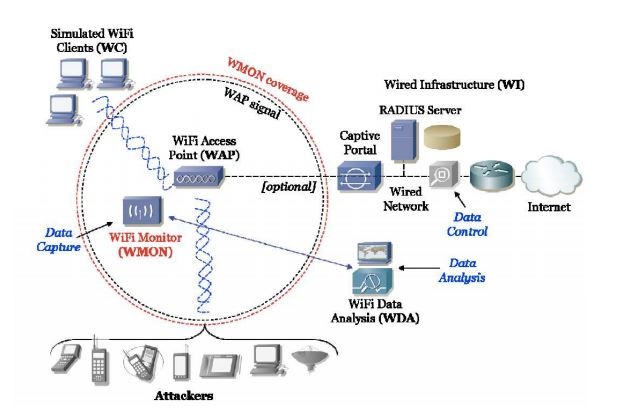
Fig: Honeyspot architecture
Well what are the typical steps in configuring a wireless honeypot?
- Run an access point. This can be done with Linux or *BSD by putting a wireless card into hostap mode and using it to create a wireless network.
- Configure and run a DHCP server. You need to determine which network the DHCP server should hand addresses out for, e.g. 192.168.0.0/16. The router and name server records need to to point to IP addresses simulate by Honeyd.
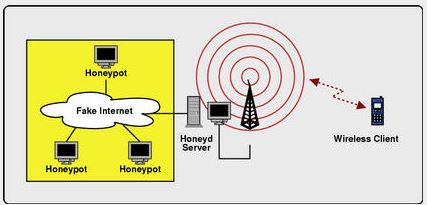
Fig: Wireless Honeypot setup configuration
- Instrument Honeyd to provide fake Internet topology. This can be achieved by configuring a virtual network topology for the whole IP address space except for the address range that is served by DHCP. Make sure that you have a name server running that resolves names. This can be done without the laptop being connected to the Internet itself.
There are different types of attack scenarios and based on which the layers of the network are configured with the deployment of the honeypots.
Related study:
http://ijns.jalaxy.com.tw/contents/ijns-v15-n5/ijns-2013-v15-n5-p373-383.pdf
http://www.diva-portal.org/smash/get/diva2:327476/fulltext01
Fig: Wireless honeypot framework
5. How to configure/Setup a simple Honeypot?
https://www.youtube.com/watch?v=zOXd35GbDKg
https://singhgurjot.wordpress.com/2014/09/22/how-to-install-honeyd-on-ubuntu-13-10/
https://gist.github.com/ozooxo/10600945
6. Honeypots securing SCADA network, how?
Supervisory Control and Data Acquisition (SCADA) is an integrated part of a process control network. SCADA has applications in many complex and critical places like nuclear power plant, electricity grid, air traffic control, satellite launch center and lot more. The "Stuxnet virus" and "Duqu" proved the need for process control network security which caused substantial damage to the Iran's nuclear program.
A typical process control network (PCN) is categorized by four levels, starting at Level 0.
Considering example as a temperature control in a factory floor-
Level 0: Temperature sensor senses the temperature of a boiler and sends the values to the controller- typically the signals are analog in nature.
Level1: Based on the sensed value required actions are executed by the controller, either regulate the temperature or turn it ON/OFF.
Level2: On the factory floor there might several of these controllers, these are connected to a centralized control system (SCADA) that supervises the control to ensure synchronization between various processes.
Level3: Here advanced controllers are deployed to optimize the processes, includes historians and optimization controllers.
Typically Level 1 to Level 3 can use the Ethernet for connectivity. The business network that is not part of the PCN is considered as Level 4, and care is taken to control access between these two networks only on a need basis. SCADA at Level 2, is one of the most important parts of the PCN. It is used to centrally monitor and record various process parameters. Here, the processes may be running at one physical location and SCADA may be located at entirely different locations. As per the requirement, WAN/LAN links are used for interconnection between them.
Honeypots/Honeynets could be deployed at level2 mimicking SCADA systems. An attacker may attack a SCADA honeypot perceiving it to be a true SCADA system.
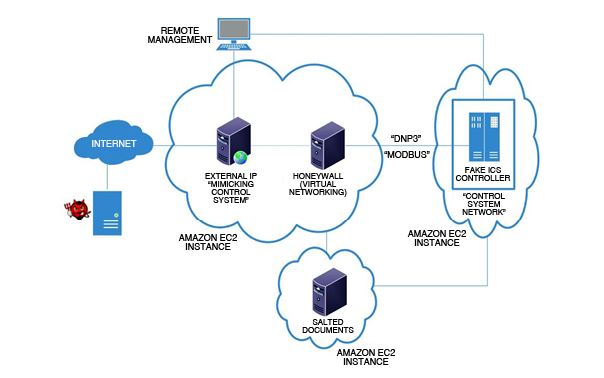
Fig: SCADA network of water pumping station attack
How to setup a honeypot on SCADA?
Honeyd: An open source honeypot
As defined by honeyd.org, Honeyd is a small daemon that creates virtual hosts on a network. These hosts can be configured to run arbitrary services, and their personality can be adapted so that they appear to be running certain operating systems.
Honeyd enables a single host to claim multiple addresses (tested up to 65536) on a LAN for network simulation. Honeyd improves cyber security by providing mechanisms for threat detection and assessment. It also deters adversaries by hiding real systems in the middle of virtual systems.
The Honeyd configuration file defines how the configured honeypot will respond to various types of requests such as ICMP Ping, requests on UDP ports, TCP SYN, etc, thus, in a way, defining the status of various ports and services. This reply is interpreted by the scanning tool as a system running a corresponding service.
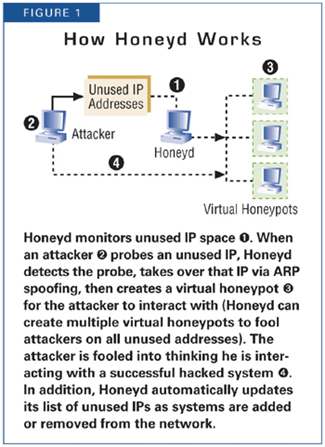
Fig: How honeyd works?
Setting up Honeyd on Ubuntu: http://opensourceforu.com/2013/12/secure-scada-network-using-honeypot/
7. Advantages and Disadvantages of setting up a honeypot.
Advantages:
1. Simple – Deploy, understand and maintain
2. Reduced False Positive - With most detection technologies (IDS, IPS) a large fraction of alerts is false warnings, while with Honeypots this doesn't hold true
3. Cost Effective
4. Collect Real Data - While Honeypots collect a small volume of data but almost all of this data is a real attack or unauthorized activity
5. IPv6 Encryption
Disadvantages:
1. Risk- A Honeypot, once attacked, can be used to attack, infiltrate, or harm other systems or organizations
2. Narrow field of View- If an attacker breaks into your network and attacks a variety of systems, your honeypot will be blissfully unaware of the activity unless it is attacked directly
3. Finger Printing - When an attacker can identify the true identity of a honeypot because it has certain expected characteristics or behaviors
4. The honeypot may be used as a zombie to reach other systems and compromise them.
This can be very dangerous.
8. Ethical concerns related to honeypots!
Every country has different laws regarding to honeypot usage and information capturing. Earlier there were some confusions on honeypot for several reasons, one the concept was very new and other of different variants of it which is deployed. Based on the use case scenarios thee are different legal issue that is concerned on the same. There are no precedents for honeypots, also there were no legal cases recorded on the issues.
There are three issues that are commonly discussed on honeypots,
1. Privacy: Since honeypots capture extensive amount of information about hackers- this can potential violate their privacy. In some cases there is exemption, meaning that security technologies can capture information on attacker identity as long as is been used to secure your environment.
2. Liability: If honeypot is used to attack or harm other systems in the network there is concern with liability on honeypots. The risk is greatest with research honeypots.
3. Entrapment: In most of the cases involving honeypots, entrapment isn't an issue. According to Lance Spitzner's The Value of Honeypots, Part Two: Honeypot Solutions and Legal Issues article, honeypots cannot be entrapment issue. Here are his three reasons why entrapment is not an issue for honeypots:
- "Honeypots do not induce or persuade anyone, they are most often production systems, or emulate production systems.
- Attackers find and attack honeypots based on their own initiative.
- Most administrators are not law enforcement. They are not using honeypots to collect evidence and prosecute. Normally they are used as a means to detect, and possibly learn about, attacks."
More detailed study:
https://link.springer.com/article/10.1186/s13635-017-0057-4
http://www.diva-portal.org/smash/get/diva2:327476/fulltext01
9. Firewall and Honeypots. How they inter-work together:
Basically a firewall is designed to keep the attackers out of the network whereas honeypots are designed to entice the hackers to attack the system.
This is done so that a security researcher can know how hackers operate and can know which systems and ports the hackers are most interested in. Also firewalls log activities and logs also contains events related to production systems.
Based on the application and size of networks honeypots are deployed either inside firewall or outside.
However in case of honeypot, the logs are only due to non-productive systems, these are the systems that no one should be interacting with. So a firewall log contains 1000 entries of all the systems of the network whereas the honeypot's log only contain 5-10 entries.
Related read: https://www.scribd.com/document/92790032/IDS-Firewall-Honeypot
10. Honeypot & automation, a bigger game!! - Communication protocols - PLC, FTP, Modbus etc.,
SCADA infrastructures mostly comprises of two levels: operations (Master stations and databases) and field networks (PLC, RTU). Various communication protocols interoperate in the infrastructure. We'll look at Modbus honeypot which is deployed at field network of SCADA system acts as a PLC.
Honeypot Front end interface:
Modbus API module specifically implements the Modbus TCP protocol variant which is widely used in ICS (Industrial Control Systems). Its ease of operation and deployment makes it to use widely.
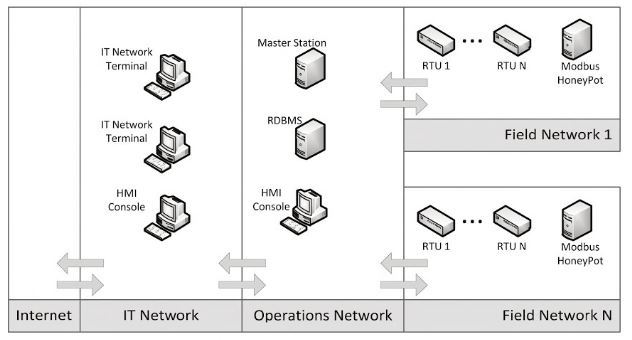
Fig: Modbus Honeypot implementation on SCADA infrastructure
There are typically four components,
1. Modbus API simulator: Receives commands and behaves like regular PLC, inhibiting minimal protocol functionality.
2. File transfer protocol (FTP) module
3. Simple Network Management Protocol (SNMP)
4. Port Scan: Detection module to detect probing activity in the TCP/IP service ports.
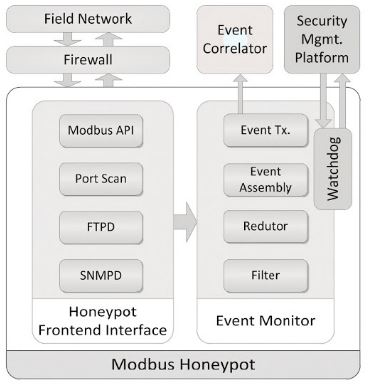
Fig: Modbus Honeypot Software architecture
Event monitor:
The information is processed at event monitor which is obtained from front end interface module. It has sub modules:
1. Filter – It filter relevant event according to pre-defined configurations
2. Reductor and Aggregator – It Processes events to aggregate the events and grouping.
3. Event assembly – It creates the security event messages using a standardized format
4. Event transmission – Ensures message transmission
The architecture is very simple and could be implemented on a simple SOC like raspberry Pi, the implementation has two Python libraries to manipulate the Modbus data (Modbus-tk-0.4.2 and pymodbus-0.9.0).
Fig: Raspberry Pi - SOC
The Modbus messages are parsed by pymodbus library, SNMPD and FTPD modules are composed by a complete service implementation and a script to check its logs – they run NET-SNMP and VSFTPd respectively.
Additionally, the scripts parses service logs, looking for activity and port Scan module uses libpcap (C-module).
References:
http://www.thewindowsclub.com/what-are-honeypots
https://en.wikipedia.org/wiki/Honeypot_(computing)
http://searchsecurity.techtarget.com/definition/honeynet
https://www.sans.org/reading-room/whitepapers/attacking/honey-pots-honey-nets-security-deception-41
http://opensourceforu.com/2013/12/secure-scada-network-using-honeypot/
http://www.honeyd.org/concepts.php
http://www.thewindowsclub.com/what-are-honeypots
http://www.informit.com/articles/article.aspx?p=30489&seqNum=2
https://www.slideshare.net/amitpoonia404/seminar-report-on-honeypot
https://pdfs.semanticscholar.org/c437/2e695acd7636367c106d6c347544ed131b98.pdf
http://www.diva-portal.org/smash/get/diva2:327476/fulltext01
http://www.honeyd.org/concepts.php
https://arxiv.org/pdf/1608.06249.pdf

