Some EnOcean Security Concerns
Some EnOcean Security Concerns
EnOcean is widely used in building automation for wireless sensing and control, particularly in retrofit applications where pulling cable is impractical. As with any wireless protocol deployed in operational technology (OT) environments, security properties must be evaluated in the context of the threat model, physical access assumptions, and the consequences of unauthorized control or denial-of-service.
The purpose of this page is to summarize a set of security concerns highlighted by the SEC Consult Vulnerability Lab. The images below are presented as reference slides and focus on practical issues that can arise when security features are optional, when key management is weak or operationally difficult, or when availability can be degraded through protocol-level behaviors.
This is an informational technical note intended for engineers, integrators, and facility security teams. It is not a claim about any specific installation. Actual risk depends on device capabilities, whether security modes are enabled, radio environment, physical access, and the surrounding controls (network segmentation, monitoring, commissioning practices, and operational procedures).
Background: Wireless OT Security Considerations
Wireless building automation systems have a different exposure profile than typical IT networks. Many field devices are installed in publicly accessible areas (corridors, mechanical rooms, tenant spaces), which increases the probability of an attacker being able to operate within RF range. In addition, wireless protocols must balance power consumption, device cost, and commissioning complexity, which can influence the practical deployment of cryptography and authentication.
When evaluating EnOcean or any similar protocol, engineers typically consider:
- Confidentiality: whether payloads can be intercepted and understood
- Integrity: whether messages can be modified or forged
- Authentication: whether devices can confirm who sent a message
- Replay resistance: whether captured messages can be resent to trigger actions
- Availability: whether the system can be disrupted or forced into failure modes
- Key management: how keys are created, distributed, rotated, and revoked
In building automation environments, the most common practical impacts are not data theft. They are unauthorized control (commands that should not be accepted), false state (incorrect sensor values that mislead control logic), and loss of availability (systems that become unreliable, forcing manual intervention).
Summary of the Highlighted Concerns
The SEC Consult slide excerpts below emphasize several recurring themes that are common across many wireless OT protocols:
- Optional security modes: If security is not enabled by default or is difficult to deploy, systems may operate in a weaker mode in the field.
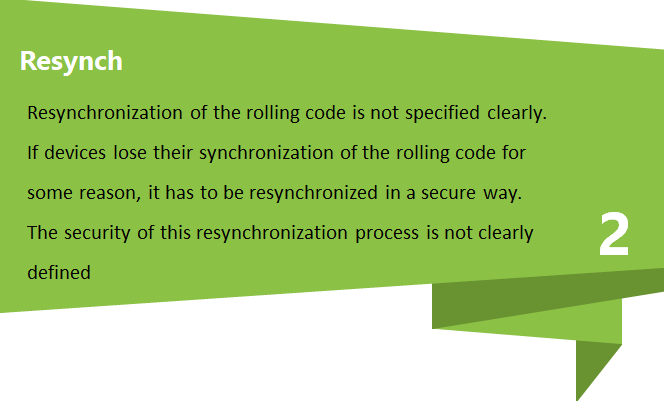
- Resynchronization behavior: Some anti-replay or rolling-code schemes require resync logic. If resynchronization can be triggered or abused, it can affect reliability or open pathways for replay-style attacks depending on the implementation.
- Blocking / availability impacts: Wireless protocols are inherently susceptible to interference and jamming. Beyond raw RF jamming, protocol-specific behaviors can also be used to degrade service or cause devices to ignore legitimate messages.
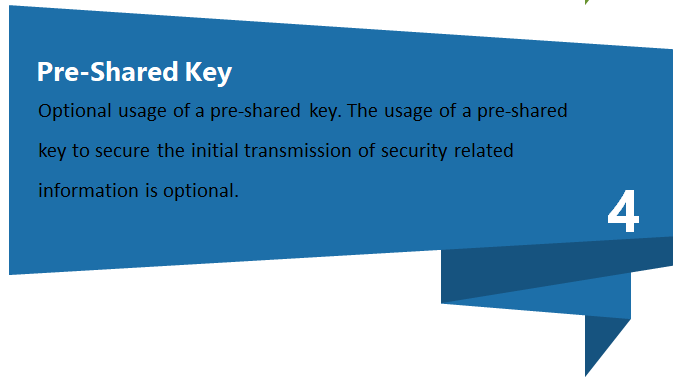
- Pre-shared keys: If a security model relies on shared secrets that are reused across devices or deployments, compromise of one key can have broader impact. Operationally, pre-shared keys can also lead to insecure storage, weak provisioning workflows, or limited rotation practices.
These issues do not necessarily mean EnOcean is unsuitable for a project. Rather, they indicate that an integrator should confirm the selected device profiles, verify security capabilities, and apply controls appropriate to the site’s risk tolerance.
Reference Slides (SEC Consult Vulnerability Lab)
From the SEC Consult Vulnerability Lab, here are the following security concerns surrounding EnOcean. The images are provided as reference material; click any image to open the full-size version.
Source: SEC Consult Vulnerability Lab (referenced via Chipkin.com page content)
Practical Mitigations for Integrators
When deploying EnOcean in facilities that have elevated security or reliability requirements, consider implementing controls that reduce exposure and improve detectability. The specific mitigation set will vary by product selection and site policy, but the following practices are commonly applied in OT environments:
- Confirm security mode usage during commissioning: Treat security enablement as a formal acceptance criterion, not an optional configuration.
- Establish key management procedures: Ensure provisioning workflows avoid reusable keys, document where secrets are stored, and define how keys can be rotated when devices are replaced.
- Segment and supervise the integration boundary: Where EnOcean bridges into BACnet, Modbus, or IP networks, treat the gateway as a security boundary and limit who can reach it and how it can be managed.
- Monitor for anomalies: Consider monitoring for unexpected device enrollments, excessive resynchronization events, repeated command bursts, or unexplained periods of radio silence.
- Plan for availability: If the application is safety-critical or mission-critical, validate behavior under interference and define fallback strategies (manual override, wired backup, alarm escalation).
In many deployments, the risk is not “remote compromise from the Internet” but local RF-range abuse. Threat modeling should therefore consider physical access, tenant access, public access, and contractor access, not only network perimeter controls.
Frequently Asked Questions (FAQ)
Does this mean EnOcean is insecure by default?
Not necessarily. The key point is that risk depends on device capabilities and how systems are commissioned. The concerns highlighted here are intended to ensure integrators validate which security features are enabled and how keys and device trust are managed in a real installation.
Why do “optional security” features matter in the field?
Optional features are often disabled due to commissioning time, compatibility issues, or limited understanding of the security model. In OT environments, security controls must be operationally feasible, or they tend not to be consistently deployed.
What is the practical impact of “blocking” concerns?
Blocking concerns generally relate to availability: preventing messages from being delivered or accepted. In building automation, this can manifest as missed sensor updates, delayed control actions, nuisance alarms, or systems falling back to conservative defaults.
Why are pre-shared keys a concern?
Pre-shared keys can be secure if they are unique per device and managed correctly. They become problematic when keys are reused, distributed insecurely, stored in plain text, or cannot be rotated. In those cases, compromise can scale beyond a single device.
Should I treat EnOcean gateways as IT devices or OT devices?
Typically both. Gateways often bridge RF networks into IP-based supervisory systems, which makes them a boundary component. Apply OT commissioning discipline and IT-style management controls (access control, patching where applicable, and configuration management).
What is the first action an integrator should take?
Identify the specific EnOcean device profiles and security modes in use, then validate during commissioning that security settings are enabled and documented. If you cannot validate security mode and key handling, assume the deployment is operating in a weaker mode and mitigate via segmentation and monitoring.