What is Signed Firmware
What is Firmware?
Firmware is a special kind of software that serves the narrow purpose of abstracting the hardware functionality for a piece of hardware. It enables high-level software development to be independent of the hardware.
What is Signed Firmware?
Signed firmware is a security measure that involves the software vendor digitally signing the firmware image using a private key. When firmware carries this cryptographic signature, a device undergoes a verification process before accepting and installing the firmware. If any discrepancies or alterations in the firmware's integrity are detected, the device will decline the firmware upgrade.
The procedure for signing firmware commences with the calculation of a cryptographic hash value. Subsequently, this value is signed using the private key of a private/public key pair, and the resulting signature is affixed to the firmware image.
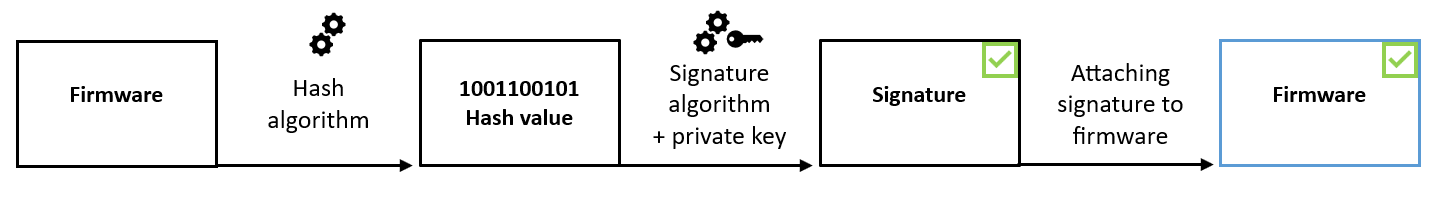
Prior to the firmware upgrade process, it is essential to verify the new firmware's authenticity. This verification involves using a public key to confirm that the hash value was signed with the corresponding private key. Additionally, by computing the hash value of the firmware and cross-referencing it with the authenticated hash value from the signature, the firmware's integrity can be ascertained.
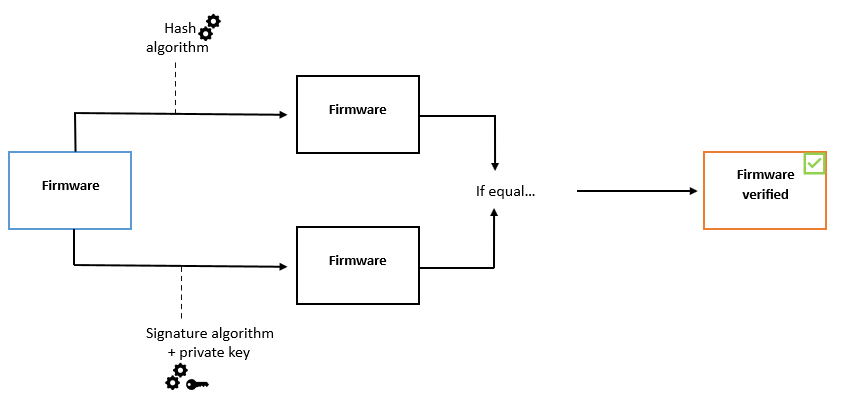
How it works?
A secure signing server signs the firmware securely. After the firmware is signed in the signing server, it travels through the supply chain, eventually reaching its destination OCP platform (or device).
There, the platform verifies the signer's digital signature. If the verification succeeds, the platform installs and / or executes the firmware. If the verification fails, because the wrong key was used, or the signature was modified, or the firmware was modified somewhere along the way, a platform policy dictates the next action, whether to reject the failing firmware, isolate it, or allow it to run.
Therefore, the security of the signing server is critical because it applies the "protective wrapper" (digital signature) that protects the firmware on its journey from the supplier to the OCP product. For this reason, the signing server must be configured securely, it must be placed in a secure environment, and there must be safeguards against its misuse by associated administrators and users.
Benefits of Digitally Signed Firmware:
- Prevents malicious modifications to the firmware which could result in: Viruses being inserted into the firmware
- Prevents Data theft
- Prevents Data Destruction
- Prevents Data Manipulation
- Protection from counterfeit drives
- Verifies the authenticity and integrity of firmware
- Enhances ability to withstand both physical and logical attacks
- Protect the private keys (even in the face of adversarial destructive analysis)
What Digitally Signed Firmware Does:
Firmware Authentication / Validity Checks are conducted before the firmware is downloaded to the drive to:
- Validate authentic firmware for the drive
- Validate firmware is genuine firmware
- Ensures firmware has been unaltered
QuickServer Signed Firmware and Secure Connections
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a security technique that allows secure data transfer across untrusted networks by establishing an encrypted connection between a server and a client.
These functions are supported on the following FieldServers; FS-QS-1011 or FS-QS-1211
The TLS Port parameter is added in the connections section of the configuration file and a port number between 1 – 65535 is set.
This sets the FieldServer to accept any incoming connection, but a client's verification certificate will not be requested. The FieldServer end-point communication will be encrypted but not authenticated.
Connections can be limited to only a particular domain (vendor devices) by using the check_Remote_Host in the configuration to specify the domain/host name.
The Check_Remote_Host (common name) can be obtained by;
- Using https://www.sslshopper.com/certificate-decoder.html to decode the certificate.
- Run (openssl x509 -in certificate.pem -text -noout) in the openssl program.
- Asking for the host name from the certificate issuer.
The certificate used must be in PEM format and can be converted using
On request, an embedded self-signed certificate can be sent.
The TLS_Port parameter can also add Validate_Client_Cert to request and verify a client's certificate against its authority file before accepting a connection. This lets the FieldServer only accept connections from other FieldServers.
The FieldServer can also accept connections from a chosen list of remote clients using the authority file containing a collection of client certificates.
Did you know that we also carry Integration Solutions?
Chipkin has integration solutions for almost every situation. We specialize in network protocol communications and have over 20+ years of experience. Click for more information:


