Are you being Tracked on Internet?
Yes, most users are tracked to some extent when using the internet. Search engines, social media platforms, and many websites collect data to improve services, personalize content, and deliver targeted advertising. While much of this tracking is conducted for legitimate commercial purposes, it can also raise privacy concerns if users are not aware of how their data is collected and used.
Companies such as Google may track information including search activity, approximate location, device characteristics, and interaction patterns. This data is often used to tailor advertisements and improve user experience. However, similar tracking techniques can also be exploited by malicious actors seeking to gather personal information or compromise devices.
Malicious tracking can occur through malware installed on computers, mobile devices, smart TVs, or other internet-connected equipment. These threats may operate silently in the background, collecting data or transmitting information without the user’s knowledge.
Monitoring Your Outgoing Network Traffic
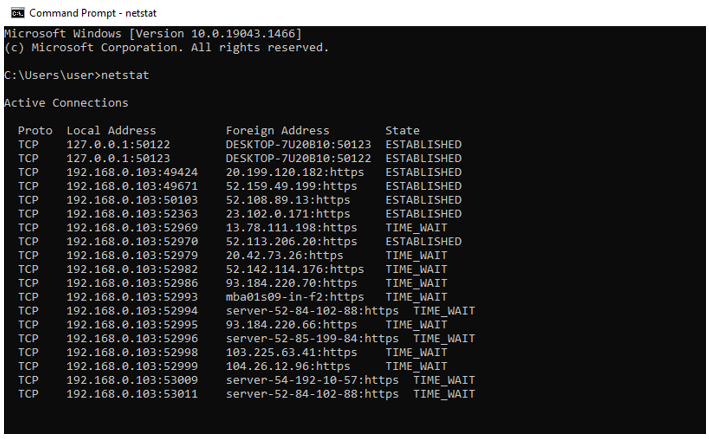
One way to better understand where your computer is communicating is by monitoring outgoing network connections. On Windows systems, this can be done using the built-in netstat command.
Open the Command Prompt and type netstat (without quotes). For best results, perform this test while only one browser window is open. The command will display a list of active network connections, including the IP addresses that your system is communicating with.
By reviewing these IP addresses, you can identify external servers receiving data from your system. Searching these IP addresses online can provide insight into the organizations or regions involved. While many connections are expected and legitimate, unfamiliar or unexpected destinations may warrant further investigation.
Identifying Potentially Malicious Software
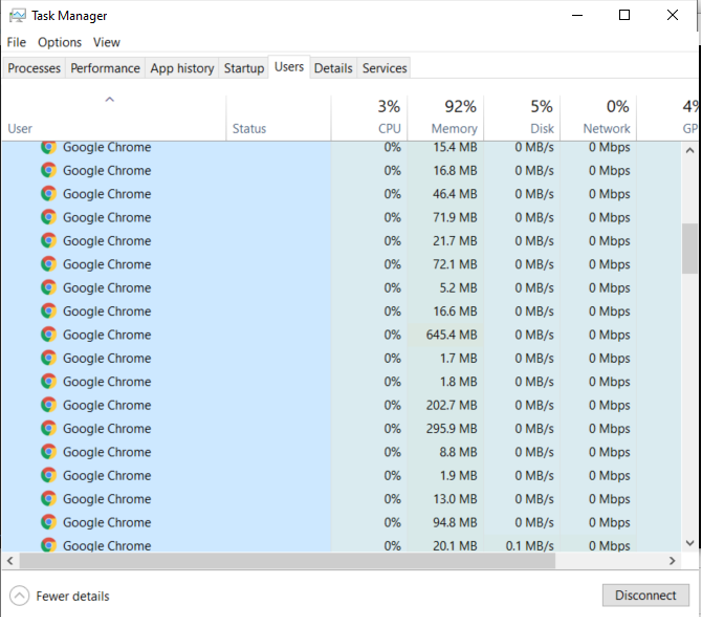
Another method for detecting suspicious activity is reviewing running processes on your system. On Windows, this can be done using the Task Manager.
Open Task Manager, navigate to the Processes tab, and enable the User Name column. This allows you to see which user account is associated with each running process.
Processes running without your user name or appearing unfamiliar may indicate background services, third-party applications, or potentially unwanted software. While not all unfamiliar processes are malicious, any suspicious entries should be researched before taking action.
Protection Measures
Reducing online tracking requires a combination of browser configuration, cautious behavior, and regular system maintenance. While it is difficult to eliminate tracking entirely, users can significantly reduce exposure by following basic best practices.
- Avoid signing in to browsers when not required. Staying signed out limits long-term profile building across browsing sessions.
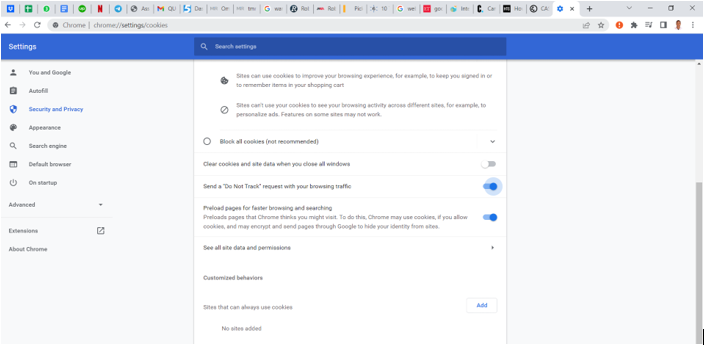
- Manage cookie tracking. Decline non-essential cookies where possible and review cookie settings regularly.
- Enable “Do Not Track” settings within your browser, understanding that compliance varies by site.
- Limit ad personalization. Review and disable personalized advertising settings when available.
Many platforms create interest-based profiles to deliver targeted advertisements. While personalization can be convenient, it also increases the amount of data collected over time. Adjusting these settings helps reduce long-term tracking exposure.
Safety Tips
Maintaining online privacy is an ongoing effort. Users should routinely scan their systems for keyloggers, spyware, and other malicious software using reputable security tools.
Keeping operating systems and applications up to date, avoiding untrusted downloads, and practicing safe browsing habits all contribute to reducing tracking risks and improving overall digital security.


