Pipeline and Industrial Hacking
Industrial Control Systems (ICS) used in critical infrastructure and manufacturing industries are targets of sophisticated cyberattacks. Industrial Hacking has emerged as a serious threat to industries around the globe. Due to the rapid development of cyber technology, Industrial hacking has become a more challenging task to be countered and which causes a significant loss to the operation and the finances of the industry.
On May 7, 2021, Colonial Pipeline, an American oil pipeline system that originates in Houston, Texas, and carries gasoline and jet fuel mainly to the Southeastern United States, suffered a ransomware cyberattack that impacted computerized equipment managing the pipeline. In response, Colonial Pipeline Company halted all of the pipeline's operations to contain the attack. Colonial Pipeline paid the requested ransom (73 bitcoin or nearly $3 million) within several hours after the attack. The hackers then sent Colonial Pipeline a software application to restore their network, but it operated very slowly.
How to prevent Industrial Hacking through our gateways?
The QuickServer is a family of high-performance, fully configurable, and cost-effective building and industrial automation IIoT gateways for integrators to easily connect to the cloud and interface devices to networks in commercial buildings, campuses, and industrial facilities.
1. USE OF SSL/TLS FOR SECURE CONNECTION
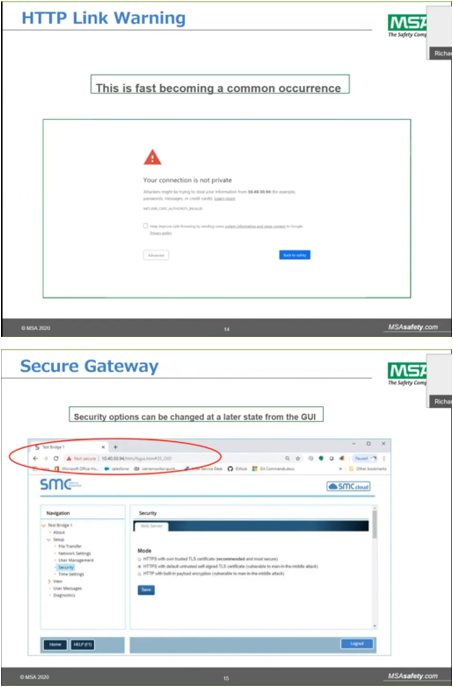
SSL/TLS (Secure Sockets Layer/Transport Layer Security) is a security technology for establishing an encrypted connection between a server and a client. This allows the secure transfer of data across untrusted networks.
- These functions are supported on the following:
- FS-QS-1010 or FS-QS-1210 with a serial number starting with 14 or later (indicating the year it shipped).
- FS-QS-1011 or FS-QS-1211 with a serial number starting with 13 or later (indicating the year it shipped).
- TLS_Port parameter: This configuration sets the FieldServer to accept any incoming connection but will not request a client's/Server's certificate for verification. This means that the FieldServer end point communication will be encrypted but not authenticated. The FieldServer will send an embedded self-signed certificate if one is requested by a connecting client.
- Limiting Client Access: This configuration sets the FieldServer to request and verify a client's certificate against its internal authority file before accepting connection. By default, this means the FieldServer will only accept connections from other FieldServers. In order to load an authority file so that the FieldServer will accept connections from a chosen list of remote clients, configure the FieldServer.
- Limit Server Access: This configuration sets the FieldServer to request and verify server's certificate against its internal authority file before finalizing the connection. By default, this means the FieldServer will only establish connections to other FieldServers.
- Cert_Authority_File: This configuration has the FieldServer accept connections from clients/servers who have the correct certificate. The authority file is a collection of client certificates in PEM format. This file can be edited using any text file editor.
- Certificate Validation Options: If connections must be limited to only a particular domain (vendor devices), include Check_Remote_Host to specify the domain/host name.
- The Check_Remote_Host value is synonymously known as common name, host name or domain etc. The common name can be obtained by the following methods:

The configuration above tells the FieldServer to only accept connections that have the correct certification and is coming from the specified host.
- Ask the certificate issuer for the host name.
- Use online tools to decode the certificate (for example: https://www.sslshopper.com/certificate-decoder.html).
- If the program openssl is installed on the local PC, then run the following command to get the common name: openssl x309 -in certificate.pem -text –noout
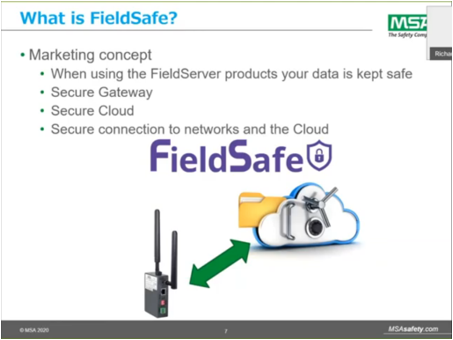
2. FIELDSAFE: The internet isn't getting any safer – so FieldServer is.
(Reference: https://us.msasafety.com/smc/fieldsafe)
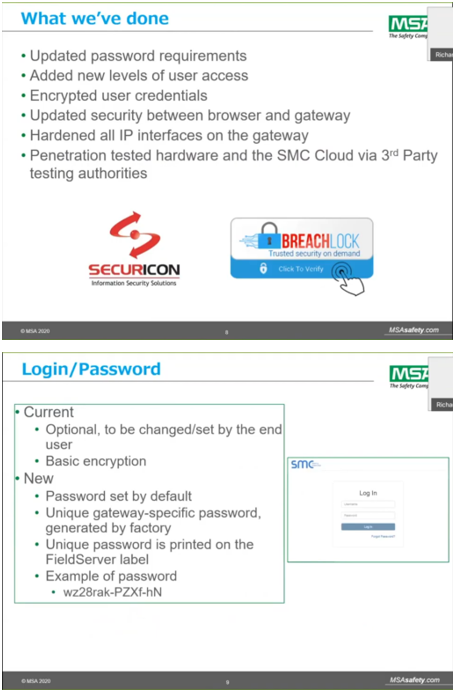
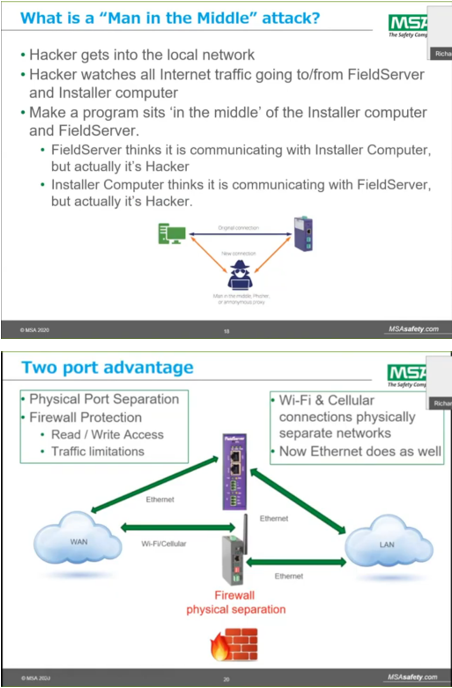
FieldSafe is a security feature set added to every FieldServer gateway. The FieldSafe feature set ensures device security in a world where cyberattacks are increasing in frequency and threats are becoming more sophisticated by securing the local hardware and the SMC Cloud application with some of the latest technologies that are currently available on the IoT marketplace.
In today's sophisticated cyber landscape, it is no longer good enough for customers to erect a virtual fence around their on-premise network. Not only are end-users accessing equipment data from several different networks and devices, but the number of internet access points within buildings is increasing. A new approach to security must be considered – one that encourages precautions implemented at every access point.
All of Sierra Monitor's multi-protocol gateways, routers, and explorers run on a high-performance engine that enables the various devices and management systems in an industrial environment to connect and communicate with one another by translating the various protocols they use to achieve complete interoperability, allowing data from any device to be readable and possibly writable by others within the ecosystem.
Whether it is an established standard, such as Modbus or BACnet, or more seldom used proprietary protocols, our multi-protocol gateways are able to convert both data and commands from any device and integrate them into one common protocol that ensures transparency from your management automation system or SCADA.